The Importance of Network Visibility and Analytics
Leveraging SD-WAN for Zero Trust Initiatives
As modern IT environments become more distributed, the attack surface and corresponding risk from them increases. Organizations can’t afford to have any blind spots and must leverage data from the network and real-time analysis to enable their zero trust initiatives.
View Infographic (.PDF)Highly Distributed Environments Create Risk
Applications are distributed across private data centers, multiple public clouds, and edge locations. In addition, employees now split their time between the office and home or remote locations. As a result, organizations now have a much larger attack surface to defend. The dynamic nature of modern application environments means services are spun up and down in seconds and applications can be easily moved.
86%
currently using two or more public cloud services to some extent (IaaS and/or PaaS).

62%
cite that 50% or fewer of their production applications/workloads are running in the public cloud.
57%
state that more than half of their workforce will be roaming users in 24 months.
Almost half (46%)
of the organizations surveyed by TechTarget’s Enterprise Strategy Group reported that they have implemented or begun to implement zero trust across their organization.

>> some of the most effective tools organizations use to enable their zero trust strategy.

25%
Zero trust network access (ZTNA)

25%
Network access control

24%
Data loss prevention

24%
Multi-factor authentication
However, More than half (54%)
of these organizations report that they have had limited success or bumps in the road during deployment.

Visibility and Analytics Are Key Capabilities
Indeed, more than half of organizations (55%) responding to an Enterprise Strategy Group research survey strongly agreed that they identify and inventory all devices on the network, while 48% of these organizations strongly agreed that they use analytics to identify anomalous behavior.
It is important that organizations just beginning their zero trust journey learn from those that have already implemented or have begun to implement zero trust initiatives across their organizations.

55%
We identify and inventory all devices on the network
48%
We use analytics to identify anomalous behavior
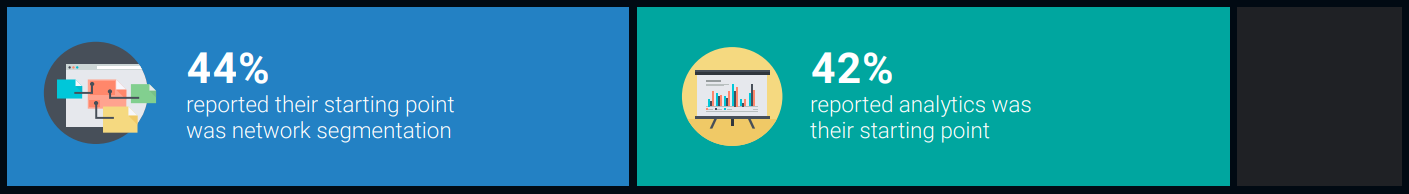
Among respondents to Enterprise Strategy Group research that have already implemented or begun to implement zero trust in their organizations:
Conclusion
Modern IT environments are highly distributed. As such, these environments are faced with an increased attack surface and increased risk to the business. To ensure a more secure environment, organizations are deploying zero trust architectures. While this encompasses a number of different technologies, organizations can leverage existing network technologies as a starting point. The ability to segment network traffic, have end-to-end visibility, and perform real-time analytics are important capabilities for enabling zero trust across an entire environment.

